
What Is a DoS Attack?
In essence, a DoS attack (Denial-of-Service attack) is a method employed to disrupt legitimate users’ access to a specific network or web resource. This is achieved by overwhelming the target, often a web server, with an immense volume of traffic or by sending malicious requests that lead to the malfunction or complete crash of the target resource.
The first recorded instance of a Denial-of-Service attack occurred in February 2000 when a 15-year-old Canadian hacker directed such an attack towards the web servers of Amazon and eBay. Since that time, the prevalence of DoS attacks has increased, with more individuals resorting to this disruptive technique to target various industries.
DoS attacks can take various forms, including volumetric attacks that flood the target with an enormous amount of traffic, protocol attacks that exploit vulnerabilities in network protocols, and application layer attacks that target specific applications or services running on the server. These attacks can cause serious disruptions, leading to financial losses, reputational damage, and significant downtime for affected organizations.
To mitigate the impact of DoS attacks, organizations implement various defense mechanisms, such as rate-limiting, traffic filtering, and load balancing, to ensure their network infrastructure can handle the sudden surge in traffic. Additionally, intrusion detection and prevention systems are utilized to identify and block suspicious traffic patterns that may indicate an ongoing or imminent DoS attack.
The continuous evolution of technology and the interconnected nature of the internet pose ongoing challenges for combating DoS attacks. As attackers refine their tactics and techniques, it becomes imperative for organizations to remain vigilant and proactive in safeguarding their digital assets and critical resources against potential disruptions caused by Denial-of-Service attacks.
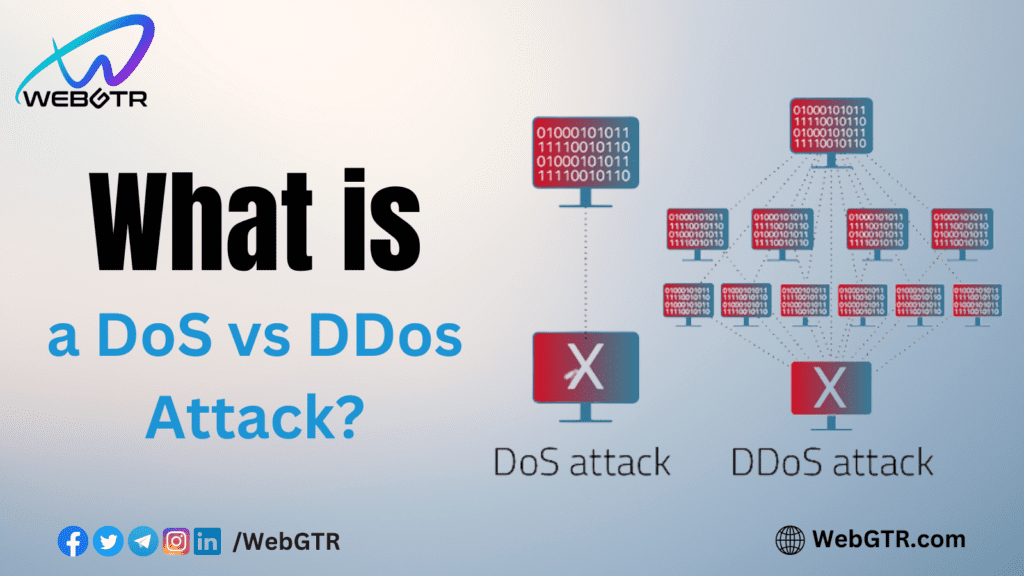
DoS vs DDoS attacks
Another related term you may come across is a DDoS attack, which stands for Distributed Denial-of-Service attack. The key distinction between a DoS and a DDoS attack lies in the number of malicious machines targeting a single resource. During a DDoS attack, numerous compromised machines are directed to overwhelm a specific target, making it far more effective in disrupting the victim compared to a DoS attack originating from a single source. The distributed nature of a DDoS attack also makes it challenging to trace back to its source, as the attack originates from multiple points.
With the increasing popularity of cryptocurrencies and crypto exchanges, they have become attractive targets for DDoS attacks. For instance, when Bitcoin Gold was officially launched, it was immediately hit by a massive DDoS attack, causing multiple hours of disruption to its website.
The Proof of Work (PoW) consensus algorithm, used by Bitcoin and other cryptocurrencies, ensures the security of network data through cryptographic proofs. This makes it exceedingly difficult to alter previously validated blocks. Attempting to change the Bitcoin blockchain would require unraveling the entire structure record-by-record, an impractical feat even for the most powerful computers.
Even in the event of a successful attack, the impact would likely be limited to modifying transactions in a few recent blocks for a short duration. Furthermore, if an attacker were to control more than 50% of the Bitcoin hashing power, attempting a so-called 51% attack (or majority attack), the underlying protocol would be promptly updated in response to the threat.
The resilience and security of PoW-based cryptocurrencies like Bitcoin rely on the vast network of decentralized nodes and the difficulty of manipulating historical transaction data. As a result, despite potential threats, these networks have proven to be remarkably robust against malicious attacks, providing users with confidence in the integrity and stability of their digital transactions.
Looking for Blockchain Development, NFTs, Website Design, Token Creation, or Other services? Reach out to us at WebGTR. Let’s discuss and bring your vision to life.
Website | Twitter | Instagram | Telegram Official Group | WhatsApp

Leave a Reply